Installations
npm install @core-js/compatDeveloper Guide
Typescript
Yes
Module System
CommonJS
Min. Node Version
^18.12.0 || >=20.0.0
Node Version
21.6.1
NPM Version
10.2.4
Score
75.3
Supply Chain
98.8
Quality
75.9
Maintenance
100
Vulnerability
100
License
Releases
3.40.0 - 2025.01.08
Published on 07 Jan 2025
3.39.0 - 2024.10.31
Published on 31 Oct 2024
3.38.1 - 2024.08.20
Published on 20 Aug 2024
3.38.0 - 2024.08.05
Published on 04 Aug 2024
3.37.1 - 2024.05.14
Published on 14 May 2024
3.37.0 - 2024.04.17
Published on 16 Apr 2024
Contributors
Languages
JavaScript (99.81%)
TypeScript (0.15%)
HTML (0.04%)
Developer
zloirock
Download Statistics
Total Downloads
583
Last Day
1
Last Week
9
Last Month
28
Last Year
583
GitHub Statistics
24,767 Stars
6,499 Commits
1,661 Forks
255 Watching
7 Branches
127 Contributors
Bundle Size
486.52 kB
Minified
53.50 kB
Minified + Gzipped
Sponsor this package
Package Meta Information
Latest Version
4.0.0-alpha.0
Package Id
@core-js/compat@4.0.0-alpha.0
Unpacked Size
522.33 kB
Size
42.22 kB
File Count
17
NPM Version
10.2.4
Node Version
21.6.1
Publised On
13 Feb 2024
Total Downloads
Cumulative downloads
Total Downloads
583
Last day
0%
1
Compared to previous day
Last week
0%
9
Compared to previous week
Last month
300%
28
Compared to previous month
Last year
0%
583
Compared to previous year
Daily Downloads
Weekly Downloads
Monthly Downloads
Yearly Downloads
Dependencies
1

I highly recommend reading this: So, what's next?
@core-js/compat package contains data about the necessity of core-js modules and API for getting a list of required core-js modules by browserslist query.
1import compat from '@core-js/compat'; 2 3const { 4 list, // array of required modules 5 targets, // object with targets for each module 6} = compat({ 7 targets: '> 1%', // browserslist query or object of minimum environment versions to support, see below 8 modules: [ // optional list / filter of modules - regex, string or an array of them: 9 'core-js/actual', // - an entry point 10 'esnext.array.unique-by', // - a module name (or just a start of a module name) 11 /^web\./, // - regex that a module name must satisfy 12 ], 13 exclude: [ // optional list / filter of modules to exclude, the signature is similar to `modules` option 14 'web.atob', 15 ], 16 version: '4.0', // used `core-js` version, by default - the latest 17 inverse: false, // inverse of the result - shows modules that are NOT required for the target environment 18}); 19 20console.log(targets); 21/* => 22{ 23 'es.error.cause': { ios: '14.5-14.8' }, 24 'es.aggregate-error.cause': { ios: '14.5-14.8' }, 25 'es.array.at': { ios: '14.5-14.8' }, 26 'es.array.find-last': { firefox: '100', ios: '14.5-14.8' }, 27 'es.array.find-last-index': { firefox: '100', ios: '14.5-14.8' }, 28 'es.array.includes': { firefox: '100' }, 29 'es.array.push': { chrome: '100', edge: '101', ios: '14.5-14.8', safari: '15.4' }, 30 'es.array.unshift': { ios: '14.5-14.8', safari: '15.4' }, 31 'es.object.has-own': { ios: '14.5-14.8' }, 32 'es.regexp.flags': { chrome: '100', edge: '101' }, 33 'es.string.at-alternative': { ios: '14.5-14.8' }, 34 'es.typed-array.at': { ios: '14.5-14.8' }, 35 'es.typed-array.find-last': { firefox: '100', ios: '14.5-14.8' }, 36 'es.typed-array.find-last-index': { firefox: '100', ios: '14.5-14.8' }, 37 'esnext.array.group': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 38 'esnext.array.group-by': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 39 'esnext.array.group-by-to-map': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 40 'esnext.array.group-to-map': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 41 'esnext.array.to-reversed': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 42 'esnext.array.to-sorted': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 43 'esnext.array.to-spliced': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 44 'esnext.array.unique-by': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 45 'esnext.array.with': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 46 'esnext.typed-array.to-reversed': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 47 'esnext.typed-array.to-sorted': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 48 'esnext.typed-array.to-spliced': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 49 'esnext.typed-array.with': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 50 'web.dom-exception.stack': { chrome: '100', edge: '101', ios: '14.5-14.8', safari: '15.4' }, 51 'web.immediate': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' }, 52 'web.structured-clone': { chrome: '100', edge: '101', firefox: '100', ios: '14.5-14.8', safari: '15.4' } 53} 54*/
targets option
targets could be a browserslist query or a targets object that specifies minimum environment versions to support:
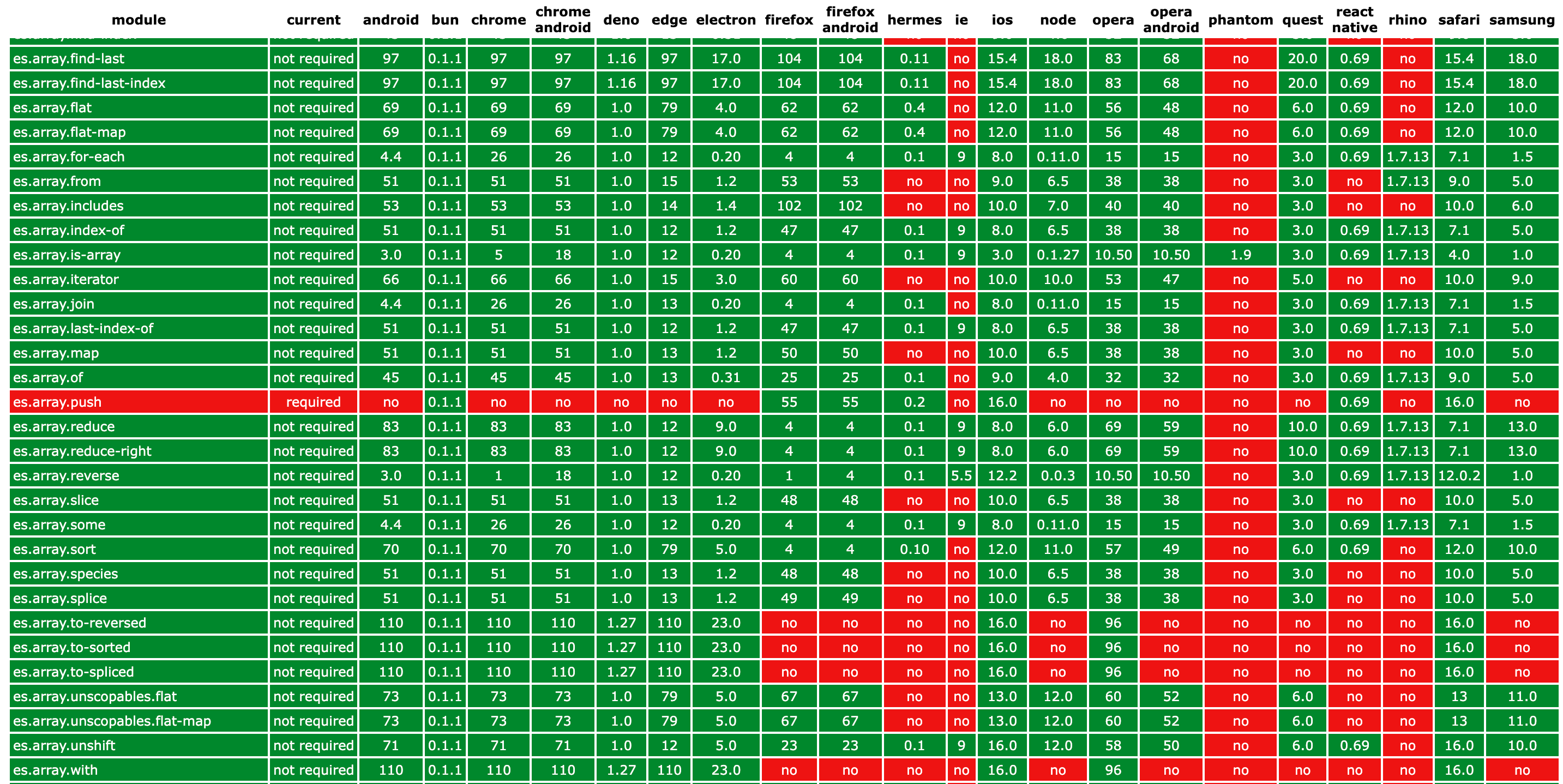
1// browserslist query: 2'defaults, not IE 11, maintained node versions' 3// object (sure, all those fields optional): 4{ 5 android: '4.0', // Android WebView version 6 bun: '0.1.2', // Bun version 7 chrome: '38', // Chrome version 8 'chrome-android': '18', // Chrome for Android version 9 deno: '1.12', // Deno version 10 edge: '13', // Edge version 11 electron: '5.0', // Electron framework version 12 firefox: '15', // Firefox version 13 'firefox-android': '4', // Firefox for Android version 14 hermes: '0.11', // Hermes version 15 ie: '8', // Internet Explorer version 16 ios: '13.0', // iOS Safari version 17 node: 'current', // NodeJS version, you can use 'current' for set it to currently used 18 opera: '12', // Opera version 19 'opera-android': '7', // Opera for Android version 20 phantom: '1.9', // PhantomJS headless browser version 21 quest: '5.0', // Meta Quest Browser version 22 'react-native': '0.70', // React Native version (default Hermes engine) 23 rhino: '1.7.13', // Rhino engine version 24 safari: '14.0', // Safari version 25 samsung: '14.0', // Samsung Internet version 26 esmodules: true, // That option set target to minimum supporting ES Modules versions of all browsers 27 browsers: '> 0.25%', // Browserslist query or object with target browsers 28}
Additional API:
1// equals of of the method from the example above 2require('@core-js/compat/compat')({ targets, modules, version }); // => { list: Array<ModuleName>, targets: { [ModuleName]: { [EngineName]: EngineVersion } } } 3// or 4require('@core-js/compat').compat({ targets, modules, version }); // => { list: Array<ModuleName>, targets: { [ModuleName]: { [EngineName]: EngineVersion } } } 5 6// full compat data: 7require('@core-js/compat/data'); // => { [ModuleName]: { [EngineName]: EngineVersion } } 8// or 9require('@core-js/compat').data; // => { [ModuleName]: { [EngineName]: EngineVersion } } 10 11// map of modules by `core-js` entry points: 12require('@core-js/compat/entries'); // => { [EntryPoint]: Array<ModuleName> } 13// or 14require('@core-js/compat').entries; // => { [EntryPoint]: Array<ModuleName> } 15 16// full list of modules: 17require('@core-js/compat/modules'); // => Array<ModuleName> 18// or 19require('@core-js/compat').modules; // => Array<ModuleName> 20 21// the subset of modules which available in the passed `core-js` version: 22require('@core-js/compat/get-modules-list-for-target-version')('4.0'); // => Array<ModuleName> 23// or 24require('@core-js/compat').getModulesListForTargetVersion('4.0'); // => Array<ModuleName>
If you wanna help to improve this data, you could take a look at the related section of CONTRIBUTING.md. The visualization of compatibility data and the browser tests runner is available here, the example:

No vulnerabilities found.
Reason
30 commit(s) and 7 issue activity found in the last 90 days -- score normalized to 10
Reason
security policy file detected
Details
- Info: security policy file detected: SECURITY.md:1
- Info: Found linked content: SECURITY.md:1
- Info: Found disclosure, vulnerability, and/or timelines in security policy: SECURITY.md:1
- Info: Found text in security policy: SECURITY.md:1
Reason
no dangerous workflow patterns detected
Reason
GitHub workflow tokens follow principle of least privilege
Details
- Info: topLevel 'contents' permission set to 'read': .github/workflows/ci.yml:6
- Info: no jobLevel write permissions found
Reason
license file detected
Details
- Info: project has a license file: LICENSE:0
- Info: FSF or OSI recognized license: MIT License: LICENSE:0
Reason
no binaries found in the repo
Reason
dependency not pinned by hash detected -- score normalized to 5
Details
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:38: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:39: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: third-party GitHubAction not pinned by hash: .github/workflows/ci.yml:43: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:60: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:61: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:83: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:84: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:12: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:13: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:17: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:27: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/ci.yml:28: update your workflow using https://app.stepsecurity.io/secureworkflow/zloirock/core-js/ci.yml/master?enable=pin
- Warn: pipCommand not pinned by hash: .github/workflows/ci.yml:22
- Info: 0 out of 11 GitHub-owned GitHubAction dependencies pinned
- Info: 0 out of 1 third-party GitHubAction dependencies pinned
- Info: 4 out of 4 npmCommand dependencies pinned
- Info: 0 out of 1 pipCommand dependencies pinned
Reason
Found 1/30 approved changesets -- score normalized to 0
Reason
no effort to earn an OpenSSF best practices badge detected
Reason
branch protection not enabled on development/release branches
Details
- Warn: branch protection not enabled for branch 'master'
- Warn: branch protection not enabled for branch 'v4'
Reason
SAST tool is not run on all commits -- score normalized to 0
Details
- Warn: 0 commits out of 1 are checked with a SAST tool
Reason
project is not fuzzed
Details
- Warn: no fuzzer integrations found
Reason
19 existing vulnerabilities detected
Details
- Warn: Project is vulnerable to: GHSA-grv7-fg5c-xmjg
- Warn: Project is vulnerable to: GHSA-952p-6rrq-rcjv
- Warn: Project is vulnerable to: GHSA-9vvw-cc9w-f27h
- Warn: Project is vulnerable to: GHSA-gxpj-cx7g-858c
- Warn: Project is vulnerable to: GHSA-h6ch-v84p-w6p9
- Warn: Project is vulnerable to: GHSA-qh2h-chj9-jffq
- Warn: Project is vulnerable to: GHSA-hxm2-r34f-qmc5
- Warn: Project is vulnerable to: GHSA-f8q6-p94x-37v3
- Warn: Project is vulnerable to: GHSA-vh95-rmgr-6w4m
- Warn: Project is vulnerable to: GHSA-xvch-5gv4-984h
- Warn: Project is vulnerable to: GHSA-w9mr-4mfr-499f
- Warn: Project is vulnerable to: GHSA-cf4h-3jhx-xvhq
- Warn: Project is vulnerable to: GHSA-pxg6-pf52-xh8x
- Warn: Project is vulnerable to: GHSA-6fx8-h7jm-663j
- Warn: Project is vulnerable to: GHSA-25hc-qcg6-38wj
- Warn: Project is vulnerable to: GHSA-cqmj-92xf-r6r9
- Warn: Project is vulnerable to: GHSA-3h5v-q93c-6h6q
- Warn: Project is vulnerable to: GHSA-p8p7-x288-28g6
- Warn: Project is vulnerable to: GHSA-72xf-g2v4-qvf3
Score
5.3
/10
Last Scanned on 2025-01-20
The Open Source Security Foundation is a cross-industry collaboration to improve the security of open source software (OSS). The Scorecard provides security health metrics for open source projects.
Learn More

