Gathering detailed insights and metrics for gulp-jira-todo
Gathering detailed insights and metrics for gulp-jira-todo
Gathering detailed insights and metrics for gulp-jira-todo
Gathering detailed insights and metrics for gulp-jira-todo
Gulp plugin for checking your JavaScript source files for comments containing TODOs that reference Jira issues.
npm install gulp-jira-todoTypescript
Module System
Min. Node Version
Node Version
NPM Version
JavaScript (100%)
Total Downloads
0
Last Day
0
Last Week
0
Last Month
0
Last Year
0
MIT License
153 Commits
1 Forks
2 Watchers
1 Branches
1 Contributors
Updated on Mar 10, 2024
Latest Version
2.0.1
Package Id
gulp-jira-todo@2.0.1
Unpacked Size
47.59 kB
Size
30.28 kB
File Count
14
NPM Version
6.14.7
Node Version
14.6.0
Cumulative downloads
Total Downloads
Last Day
0%
NaN
Compared to previous day
Last Week
0%
NaN
Compared to previous week
Last Month
0%
NaN
Compared to previous month
Last Year
0%
NaN
Compared to previous year
5
5
Check your JavaScript source files for comments containing TODOs that reference Jira issues. Causes warnings if the status of a referenced issue is "Open" (or any other number of configurable statuses).
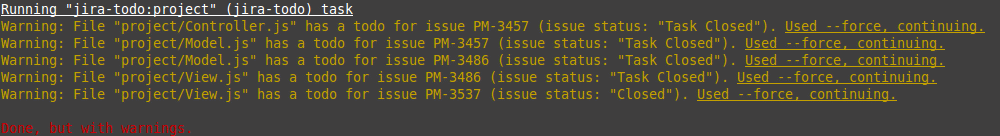
This package is intended to be used with gulp.
Install it with:
1npm install gulp-jira-todo --save-dev
You also need an external TODO parser like gulp-todo:
1npm install gulp-todo --save-dev
You can integrate it in your gulp setup like this:
1var gulp = require('gulp'), 2 todo = require('gulp-todo'), 3 jiraTodo = require('gulp-jira-todo'); 4 5gulp.task('todo', function () { 6 return gulp.src('mySources/**/*.js') 7 .pipe(todo()) 8 .pipe(jiraTodo({ 9 issueRequired: true, 10 projects: ['ABC'], 11 allowedStatuses: [1, 3], 12 allowedIssueTypes: [1, 3, 4, 5], 13 jiraUrl: 'https://jira.example.com', 14 jiraUsername: 'myJiraAccount', 15 jiraPassword: 'secretJiraPassword' // (see Security Notes below!) 16 })); 17});
Type: Array
Default value: []
An array of strings specifying the keys of Jira projects you want to check against. For example, if your application is referencing the issues MA-123 and PT-99, set this to ['MA', 'PT']. Any other issue keys (e.g. ABC-42) will be ignored.
Type: Array
Default value: [1]
An array of ids that specifies which statuses are allowed for issues that are referenced from a todo. The default 1 corresponds to the standard Jira issue status Open.
Type: Array
Default value: [1, 3, 4, 5]
An array of ids that specifies which issue types are allowed to be referenced from a todo. The default corresponds to the standard Jira issue types Bug, Task, Improvement and Sub-task.
Type: boolean
Default value: false
If enabled, all comments that match opts.todoRegex must contain at least one issue key matching the specified project(s).
Type: String
Default value: '(?<key>(?<project>[A-Z][_A-Z0-9]*)-(?<number>\\d+))'
The regular expression used to identify issue keys. By default this plugin matches strings that starts with a letter, followed by any number of alphanumeric characters, a dash and at least one digit (ignoring case). You can tweak this expression as needed, as long as you keep the named groups key, project and number. The flags g (global) and i (ignore case) are added automatically. Please refer to the XRegExp documentation for further details.
Type: String
Default value: none
The URL of the Jira server, e.g. 'https://jira.example.com'. The path for the REST endpoint (i.e. '/rest/api/2') will be added automatically.
Type: String
Default value: none
The username used for HTTP basic access authentication.
Type: String
Default value: none
The password used for HTTP basic access authentication.
It is strongly recommended not to put your Jira credentials in your repository. Instead, create a separate JSON file, add it to your .gitignore and read the username and password from there.
For help, please read this: https://help.github.com/articles/remove-sensitive-data/
Also, make sure you use a secure connection (i.e. https) to protect your username and password.
In lieu of a formal style guide, take care to maintain the existing coding style.
Add unit tests for any new or changed functionality.
Lint and test your code using npm run lint and npm test.
See Changelog.md

No vulnerabilities found.
Reason
no dangerous workflow patterns detected
Reason
no binaries found in the repo
Reason
license file detected
Details
Reason
dependency not pinned by hash detected -- score normalized to 3
Details
Reason
project is archived
Details
Reason
detected GitHub workflow tokens with excessive permissions
Details
Reason
no effort to earn an OpenSSF best practices badge detected
Reason
security policy file not detected
Details
Reason
project is not fuzzed
Details
Reason
branch protection not enabled on development/release branches
Details
Reason
SAST tool is not run on all commits -- score normalized to 0
Details
Reason
27 existing vulnerabilities detected
Details
Score
Last Scanned on 2025-07-07
The Open Source Security Foundation is a cross-industry collaboration to improve the security of open source software (OSS). The Scorecard provides security health metrics for open source projects.
Learn More