Installations
npm install vega-functionsDeveloper
Developer Guide
Module System
CommonJS
Min. Node Version
Typescript Support
No
Node Version
20.12.2
NPM Version
lerna/7.4.2/node@v20.12.2+arm64 (darwin)
Statistics
11,260 Stars
6,450 Commits
1,505 Forks
289 Watching
52 Branches
142 Contributors
Updated on 27 Nov 2024
Languages
JavaScript (74.38%)
TypeScript (24.34%)
HTML (1.1%)
Shell (0.18%)
Total Downloads
Cumulative downloads
Total Downloads
37,102,883
Last day
-2.9%
27,387
Compared to previous day
Last week
-2.2%
143,551
Compared to previous week
Last month
5.9%
644,004
Compared to previous month
Last year
1.1%
8,478,467
Compared to previous year
Daily Downloads
Weekly Downloads
Monthly Downloads
Yearly Downloads
Vega: A Visualization Grammar 
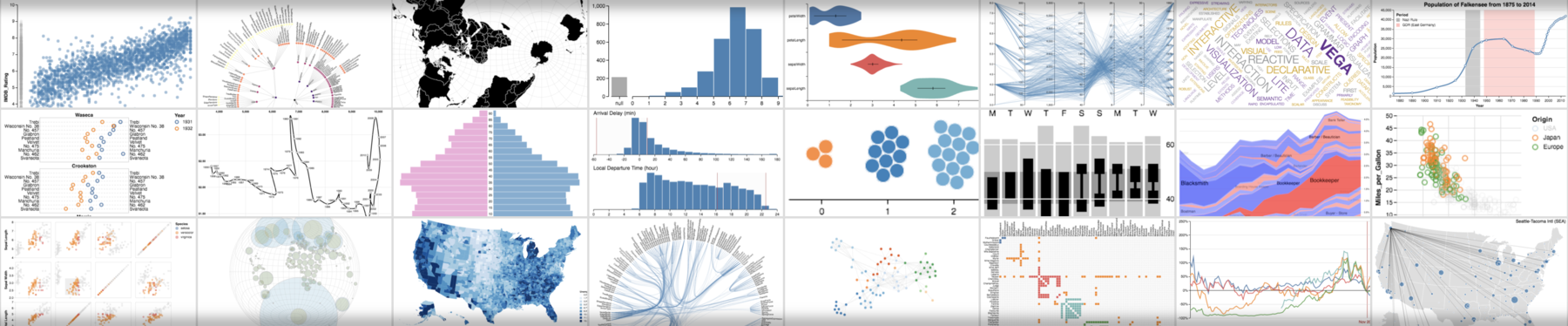
Vega is a visualization grammar, a declarative format for creating, saving, and sharing interactive visualization designs. With Vega you can describe data visualizations in a JSON format, and generate interactive views using either HTML5 Canvas or SVG.
For documentation, tutorials, and examples, see the Vega website. For a description of changes between Vega 2 and later versions, please refer to the Vega Porting Guide.
Build Instructions
For a basic setup allowing you to build Vega and run examples:
- Clone
https://github.com/vega/vega. - Run
yarnto install dependencies for all packages. If you don't have yarn installed, see https://yarnpkg.com/en/docs/install. We use Yarn workspaces to manage multiple packages within this monorepo. - Once installation is complete, run
yarn testto run test cases, or runyarn buildto build output files for all packages. - After running either
yarn testoryarn build, runyarn serveto launch a local web server — your default browser will open and you can browse to the"test"folder to view test specifications.
This repository includes the Vega website and documentation in the docs folder. To launch the website locally, first run bundle install in the docs folder to install the necessary Jekyll libraries. Afterwards, use yarn docs to build the documentation and launch a local webserver. After launching, you can open http://127.0.0.1:4000/vega/ to see the website.
Internet Explorer Support
For backwards compatibility, Vega includes a babel-ified IE-compatible version of the code in the packages/vega/build-es5 directory. Older browser would also require several polyfill libraries:
1<script src="https://cdnjs.cloudflare.com/ajax/libs/babel-polyfill/7.4.4/polyfill.min.js"></script> 2<script src="https://cdn.jsdelivr.net/npm/regenerator-runtime@0.13.3/runtime.min.js"></script> 3<script src="https://cdn.jsdelivr.net/npm/whatwg-fetch@3.0.0/dist/fetch.umd.min.js"></script>
Contributions, Development, and Support
Interested in contributing to Vega? Please see our contribution and development guidelines, subject to our code of conduct.
Looking for support, or interested in sharing examples and tips? Post to the Vega discussion forum or join the Vega slack organization! We also have examples available as Observable notebooks.
If you're curious about system performance, see some in-browser benchmarks. Read about future plans in our roadmap.
Stable Version
The latest stable version of the package.
Stable Version
5.15.0
MODERATE
2
6.1/10
Summary
Vega Expression Language `scale` expression function Cross Site Scripting
Affected Versions
< 5.13.1
Patched Versions
5.13.1
6.1/10
Summary
Vega has Cross-site Scripting vulnerability in `lassoAppend` function
Affected Versions
< 5.13.1
Patched Versions
5.13.1
Reason
4 commit(s) and 11 issue activity found in the last 90 days -- score normalized to 10
Reason
no dangerous workflow patterns detected
Reason
GitHub workflow tokens follow principle of least privilege
Details
- Info: topLevel 'pull-requests' permission set to 'read': .github/workflows/check-pr.yml:11
- Info: topLevel 'contents' permission set to 'read': .github/workflows/test.yml:10
- Info: no jobLevel write permissions found
Reason
no binaries found in the repo
Reason
license file detected
Details
- Info: project has a license file: LICENSE:0
- Info: FSF or OSI recognized license: BSD 3-Clause "New" or "Revised" License: LICENSE:0
Reason
Found 24/26 approved changesets -- score normalized to 9
Reason
no effort to earn an OpenSSF best practices badge detected
Reason
security policy file not detected
Details
- Warn: no security policy file detected
- Warn: no security file to analyze
- Warn: no security file to analyze
- Warn: no security file to analyze
Reason
dependency not pinned by hash detected -- score normalized to 0
Details
- Warn: third-party GitHubAction not pinned by hash: .github/workflows/check-pr.yml:18: update your workflow using https://app.stepsecurity.io/secureworkflow/vega/vega/check-pr.yml/main?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/test.yml:23: update your workflow using https://app.stepsecurity.io/secureworkflow/vega/vega/test.yml/main?enable=pin
- Warn: GitHub-owned GitHubAction not pinned by hash: .github/workflows/test.yml:32: update your workflow using https://app.stepsecurity.io/secureworkflow/vega/vega/test.yml/main?enable=pin
- Info: 0 out of 2 GitHub-owned GitHubAction dependencies pinned
- Info: 0 out of 1 third-party GitHubAction dependencies pinned
Reason
SAST tool is not run on all commits -- score normalized to 0
Details
- Warn: 0 commits out of 30 are checked with a SAST tool
Reason
project is not fuzzed
Details
- Warn: no fuzzer integrations found
Reason
12 existing vulnerabilities detected
Details
- Warn: Project is vulnerable to: GHSA-8hc4-vh64-cxmj
- Warn: Project is vulnerable to: GHSA-grv7-fg5c-xmjg
- Warn: Project is vulnerable to: GHSA-3xgq-45jj-v275
- Warn: Project is vulnerable to: GHSA-ghr5-ch3p-vcr6
- Warn: Project is vulnerable to: GHSA-2p57-rm9w-gvfp
- Warn: Project is vulnerable to: GHSA-952p-6rrq-rcjv
- Warn: Project is vulnerable to: GHSA-9wv6-86v2-598j
- Warn: Project is vulnerable to: GHSA-p8p7-x288-28g6
- Warn: Project is vulnerable to: GHSA-gcx4-mw62-g8wm
- Warn: Project is vulnerable to: GHSA-f5x3-32g6-xq36
- Warn: Project is vulnerable to: GHSA-72xf-g2v4-qvf3
- Warn: Project is vulnerable to: GHSA-3h5v-q93c-6h6q
Score
5.8
/10
Last Scanned on 2024-11-18
The Open Source Security Foundation is a cross-industry collaboration to improve the security of open source software (OSS). The Scorecard provides security health metrics for open source projects.
Learn More