Installations
npm install budoDeveloper Guide
Typescript
No
Module System
CommonJS
Node Version
16.13.0
NPM Version
8.1.0
Score
62.8
Supply Chain
88.8
Quality
71.1
Maintenance
100
Vulnerability
96.4
License
Releases
Contributors
Unable to fetch Contributors
Languages
JavaScript (99.41%)
HTML (0.55%)
CSS (0.04%)
validate.email 🚀
Verify real, reachable, and deliverable emails with instant MX records, SMTP checks, and disposable email detection.
Developer
mattdesl
Download Statistics
Total Downloads
2,490,765
Last Day
1,442
Last Week
8,696
Last Month
41,017
Last Year
441,618
GitHub Statistics
MIT License
2,178 Stars
566 Commits
106 Forks
33 Watchers
13 Branches
29 Contributors
Updated on Feb 11, 2025
Package Meta Information
Latest Version
11.8.4
Package Id
budo@11.8.4
Unpacked Size
86.71 kB
Size
28.91 kB
File Count
23
NPM Version
8.1.0
Node Version
16.13.0
Total Downloads
Cumulative downloads
Total Downloads
2,490,765
Last Day
-14.2%
1,442
Compared to previous day
Last Week
-8.7%
8,696
Compared to previous week
Last Month
17%
41,017
Compared to previous month
Last Year
-7.5%
441,618
Compared to previous year
Daily Downloads
Weekly Downloads
Monthly Downloads
Yearly Downloads
Dependencies
30
budō
This is a browserify development server focused on incremental reloading, LiveReload integration (including CSS injection) and other high-level features for rapid prototyping.
To install it globally:
1npm install budo -g
Running budo will start a server with a default index.html and incrementally bundle your source on filesave. The requests are delayed until the bundle has finished, so you won't be served stale or empty bundles if you refresh the page mid-update. Examples:
1# serve file on port 9966 and open browser 2budo index.js --open 3 4# enable LiveReload on HTML/CSS/JS file changes 5budo index.js --live 6 7# default html will use src="static/bundle.js" 8budo src/index.js:static/bundle.js 9 10# pass some options to browserify 11budo index.js --live -- -t babelify 12 13# use HTTPS and enable CORS headers 14budo index.js --ssl --cors 15 16# LiveReload public directory without any bundling 17# Add all extensions of file types you want to trigger reloads 18budo --dir public/ --wg **/*.{html,css,js} --live
Then open http://localhost:9966/ to see the content in action.
By default, budo pretty-prints to terminal with garnish.

See docs for more details and integrations, such as React Hot Module Replacement, Pushstate Servers and HTTPS. PRs/suggestions/comments welcome.
features
At a glance:
- serves a default
index.html - fast incremental bundling, suspending the response until the new source is ready
- watches HTML and CSS files for changes; CSS is injected without reloading the page
- can emit ndjson logs to use another pretty-printer, like bistre.
- provides clear error messaging during development in DOM and console
- supports SSL and can generate a self-signed certificate
- the rich API allows you to build more complex development tools on top of budo
Below is an example of how syntax errors look during development, using the babelify transform.
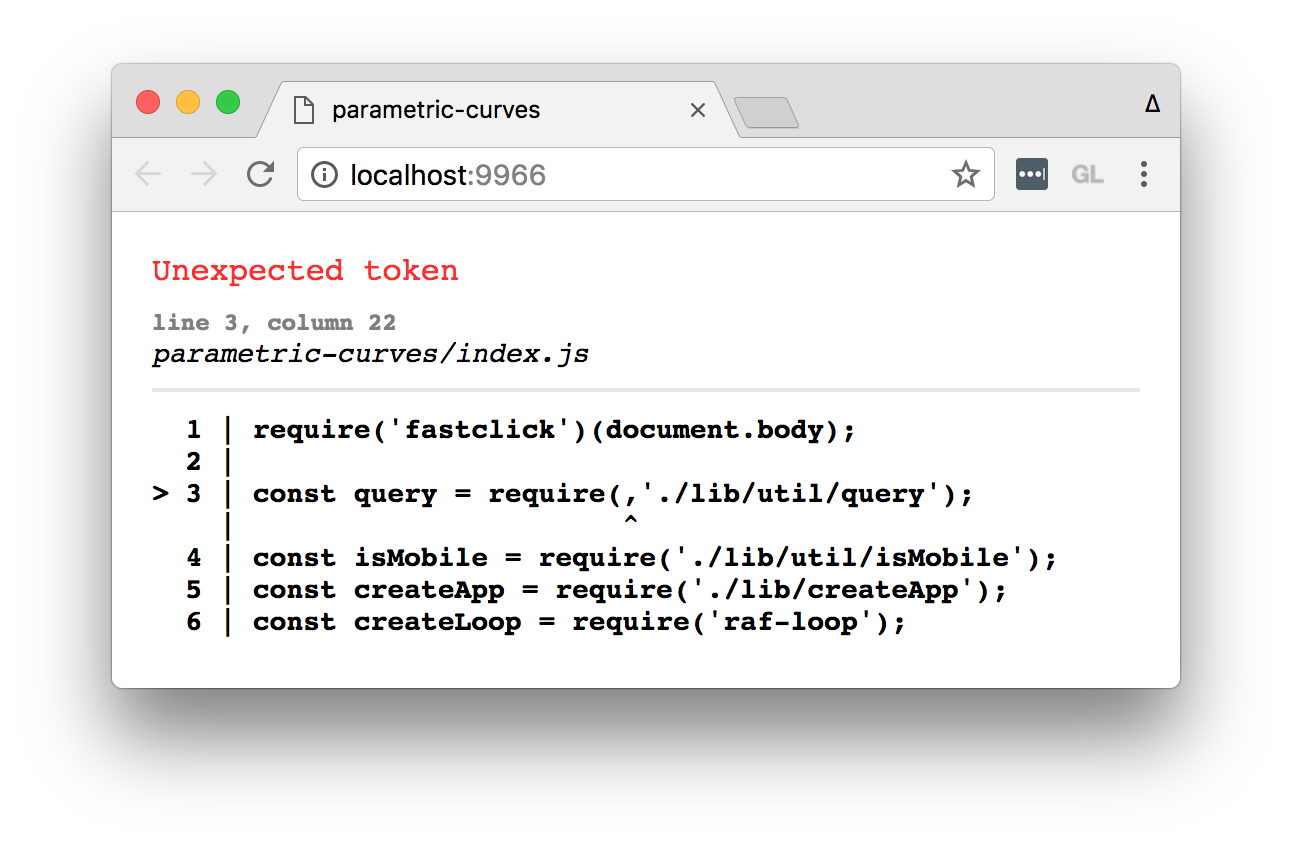
docs
- command line usage
- API usage
- running tests and examples
- rapid prototyping with budō
- experimental script injection with budo-chrome
usage
CLI
Details for budo command-line interface.
1Usage: 2 budo index.js [opts] -- [browserify opts] 3 4Options: 5 --help, -h show help message 6 --version show version 7 --port, -p the port to run, default 9966 8 --host, -H the host, default internal IP (localhost) 9 --dir, -d a path, or array of paths for base static content 10 --serve, -s override the bundle path being served 11 --live, -l enable default LiveReload integration 12 --live-port, -L the LiveReload port, default 35729 13 --open, -o launch the browser once connected 14 --pushstate, -P always render the index page instead of a 404 page 15 --base set the base path for the generated HTML, default to '/' 16 --onupdate a shell command to trigger on bundle update 17 --poll=N use polling for file watch, with optional interval N 18 --title optional title for default index.html 19 --css optional stylesheet href for default index.html 20 --ssl, -S create an HTTPS server instead of HTTP 21 --cert, -C the cert for SSL (default cert.pem) 22 --key, -K the key for SSL (default key.pem) 23 --cors set header to use CORS (Access-Control-Allow-Origin: *) 24 --ndjson print ndjson instead of pretty-printed logs 25 --verbose, -v also include debug messages 26 --force-default-index always serve a generated index.html instead of a static one 27 --no-stream do not print messages to stdout 28 --no-debug do not use inline source maps 29 --no-portfind will not attempt auto-portfinding 30 --no-error-handler disable default DOM error handling 31 --watch-glob, --wg glob(s) to watch for reloads, default '**/*.{html,css}' 32 --static-options subarg options to pass to serve-static module
By default, messages will be printed to process.stdout, and --debug will be sent to browserify (for source maps). You can turn these off with --no-stream and --no-debug, respectively.
Everything after -- is passed directly to browserify. Example:
1budo index.js --live -- -t [ babelify --extensions .es6 ]
API
The API mirrors the CLI except it does not write to process.stdout by default.
1var budo = require('budo') 2var babelify = require('babelify') 3 4budo('./src/index.js', { 5 live: true, // setup live reload 6 port: 8000, // use this port 7 browserify: { 8 transform: babelify // ES6 9 } 10}).on('connect', function (ev) { 11 console.log('Server running on %s', ev.uri) 12 console.log('LiveReload running on port %s', ev.livePort) 13}).on('update', function (buffer) { 14 console.log('bundle - %d bytes', buffer.length) 15})
See API usage for details.
See Also
budō combines several smaller and less opinionated modules.
- watchify-middleware - the underlying request handler for serving incremental reloads
- watchify-server - a less opinionated alternative to budo, built on the same underlying modules
- simple-html-index - a stream for a default
index.htmlfile
Also, special thanks to beefy and wzrd which originally inspired budo.
License
MIT, see LICENSE.md for details.

No vulnerabilities found.
Reason
no binaries found in the repo
Reason
license file detected
Details
- Info: project has a license file: LICENSE.md:0
- Info: FSF or OSI recognized license: MIT License: LICENSE.md:0
Reason
Found 5/26 approved changesets -- score normalized to 1
Reason
0 commit(s) and 0 issue activity found in the last 90 days -- score normalized to 0
Reason
no effort to earn an OpenSSF best practices badge detected
Reason
security policy file not detected
Details
- Warn: no security policy file detected
- Warn: no security file to analyze
- Warn: no security file to analyze
- Warn: no security file to analyze
Reason
project is not fuzzed
Details
- Warn: no fuzzer integrations found
Reason
branch protection not enabled on development/release branches
Details
- Warn: branch protection not enabled for branch 'master'
Reason
SAST tool is not run on all commits -- score normalized to 0
Details
- Warn: 0 commits out of 9 are checked with a SAST tool
Reason
24 existing vulnerabilities detected
Details
- Warn: Project is vulnerable to: GHSA-v88g-cgmw-v5xw
- Warn: Project is vulnerable to: GHSA-67hx-6x53-jw92
- Warn: Project is vulnerable to: GHSA-grv7-fg5c-xmjg
- Warn: Project is vulnerable to: GHSA-x9w5-v3q2-3rhw
- Warn: Project is vulnerable to: GHSA-3xgq-45jj-v275
- Warn: Project is vulnerable to: GHSA-434g-2637-qmqr
- Warn: Project is vulnerable to: GHSA-49q7-c7j4-3p7m
- Warn: Project is vulnerable to: GHSA-977x-g7h5-7qgw
- Warn: Project is vulnerable to: GHSA-f7q4-pwc6-w24p
- Warn: Project is vulnerable to: GHSA-fc9h-whq2-v747
- Warn: Project is vulnerable to: GHSA-vjh7-7g9h-fjfh
- Warn: Project is vulnerable to: GHSA-4gmj-3p3h-gm8h
- Warn: Project is vulnerable to: GHSA-9c47-m6qq-7p4h
- Warn: Project is vulnerable to: GHSA-952p-6rrq-rcjv
- Warn: Project is vulnerable to: GHSA-f8q6-p94x-37v3
- Warn: Project is vulnerable to: GHSA-hrpp-h998-j3pp
- Warn: Project is vulnerable to: GHSA-p8p7-x288-28g6
- Warn: Project is vulnerable to: GHSA-c2qf-rxjj-qqgw
- Warn: Project is vulnerable to: GHSA-m6fv-jmcg-4jfg
- Warn: Project is vulnerable to: GHSA-cm22-4g7w-348p
- Warn: Project is vulnerable to: GHSA-72xf-g2v4-qvf3
- Warn: Project is vulnerable to: GHSA-w5p7-h5w8-2hfq
- Warn: Project is vulnerable to: GHSA-j8xg-fqg3-53r7
- Warn: Project is vulnerable to: GHSA-3h5v-q93c-6h6q
Score
1.9
/10
Last Scanned on 2025-02-24
The Open Source Security Foundation is a cross-industry collaboration to improve the security of open source software (OSS). The Scorecard provides security health metrics for open source projects.
Learn More




