Gathering detailed insights and metrics for duplicate-package-checker-webpack-plugin
Gathering detailed insights and metrics for duplicate-package-checker-webpack-plugin
Gathering detailed insights and metrics for duplicate-package-checker-webpack-plugin
Gathering detailed insights and metrics for duplicate-package-checker-webpack-plugin
@types/duplicate-package-checker-webpack-plugin
TypeScript definitions for duplicate-package-checker-webpack-plugin
@cerner/duplicate-package-checker-webpack-plugin
Webpack plugin that warns you when multiple versions of the same package exist in a build.
clam-duplicate-package-checker-webpack-plugin
Webpack plugin that warns you when multiple versions of the same package exist in a build.
@barbuza/duplicate-package-checker-webpack-plugin
Webpack plugin that warns you when multiple versions of the same package exist in a build.
🕵️ Webpack plugin that warns you when a build contains multiple versions of the same package
npm install duplicate-package-checker-webpack-pluginTypescript
Module System
Node Version
NPM Version
JavaScript (100%)
Total Downloads
0
Last Day
0
Last Week
0
Last Month
0
Last Year
0
MIT License
708 Stars
41 Commits
31 Forks
5 Watchers
26 Branches
5 Contributors
Updated on Jan 13, 2025
Latest Version
3.0.0
Package Id
duplicate-package-checker-webpack-plugin@3.0.0
Size
48.04 kB
NPM Version
5.6.0
Node Version
9.5.0
Published on
Mar 20, 2018
Cumulative downloads
Total Downloads
Last Day
0%
NaN
Compared to previous day
Last Week
0%
NaN
Compared to previous week
Last Month
0%
NaN
Compared to previous month
Last Year
0%
NaN
Compared to previous year
Webpack plugin that warns when your bundle contains multiple versions of the same package.
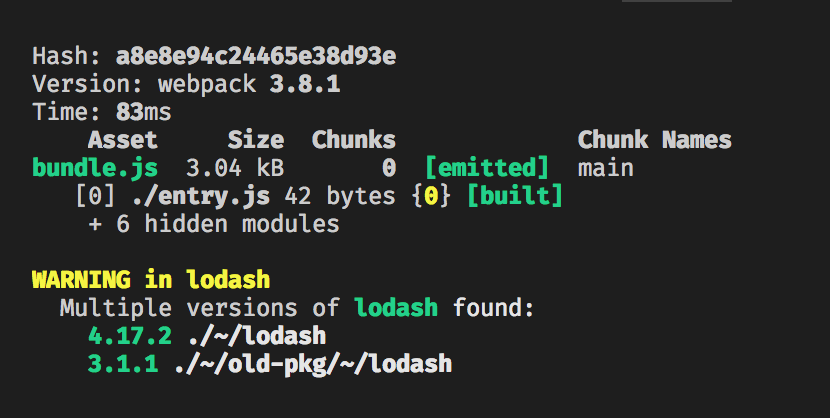
It might be possible that a single package gets included multiple times in a Webpack bundle due to different package versions. This situation may happen without any warning, resulting in extra bloat in your bundle and may lead to hard-to-find bugs.
This plugin will warn you of such cases to minimize bundle size and avoid bugs caused by unintended duplicate packages.
Motivation: https://github.com/webpack/webpack/issues/385 and https://github.com/webpack/webpack/issues/646.
1npm install duplicate-package-checker-webpack-plugin --save-dev
Add the plugin to your webpack config:
1var DuplicatePackageCheckerPlugin = require("duplicate-package-checker-webpack-plugin"); 2 3module.exports = { 4 plugins: [new DuplicatePackageCheckerPlugin()] 5};
You can also pass an object with configurable options:
1new DuplicatePackageCheckerPlugin({ 2 // Also show module that is requiring each duplicate package (default: false) 3 verbose: true, 4 // Emit errors instead of warnings (default: false) 5 emitError: true, 6 // Show help message if duplicate packages are found (default: true) 7 showHelp: false, 8 // Warn also if major versions differ (default: true) 9 strict: false, 10 /** 11 * Exclude instances of packages from the results. 12 * If all instances of a package are excluded, or all instances except one, 13 * then the package is no longer considered duplicated and won't be emitted as a warning/error. 14 * @param {Object} instance 15 * @param {string} instance.name The name of the package 16 * @param {string} instance.version The version of the package 17 * @param {string} instance.path Absolute path to the package 18 * @param {?string} instance.issuer Absolute path to the module that requested the package 19 * @returns {boolean} true to exclude the instance, false otherwise 20 */ 21 exclude(instance) { 22 return instance.name === "fbjs"; 23 } 24});
Strict mode warns when multiple packages with different major versions (such as v1.0.0 vs v2.0.0) exist in the bundle.
Packages with different major versions introduce backward incompatible changes and require either interventions on third-party packages or unsafe workarounds (such as resolving differing package major versions dependencies with a single version).
It is suggested that strict mode is kept enabled since this improves visibility into your bundle and can help in solving and identifying potential issues.
There are multiple ways you can go about resolving duplicate packages in your bundle, the right solution mostly depends on what tools you're using and on each particular case.
resolve.aliasAdd an entry in resolve.alias which will configure Webpack to route any package references to a single specified path.
For example, if Lodash is duplicated in your bundle, the following configuration would render all Lodash imports to always refer to the Lodash instance found at ./node_modules/lodash.
alias: {
lodash: path.resolve(__dirname, 'node_modules/lodash'),
}
Note: Aliasing packages with different major versions may break your app. Use only if you're sure that all required versions are compatible, at least in the context of your app
install --flatYarn allows flat installations (yarn install --flat) which will only allow one version of each package to be installed.
If you want more control over your overridden dependency versions and don't feel like using yarn install --flat, yarn supports "selective version resolution" which allows you to enforce specific versions for each dependency.
package.json
{
"dependencies": {
"lodash": "4.17.0",
"old-package-with-old-lodash": "*"
},
"resolutions": {
"old-package-with-old-lodash/lodash": "4.17.0"
}
}
If you use NPM and not Yarn, you can try running npm dedupe. NPM may leave multiple versions of the same package installed even if a single version satisfies each semver of all of its dependants.
If your project is using an old version of a package and a dependency is using a newer version of that package, consider upgrading your project to use the newer version.
If your project has a dependency and it's using an outdated version of a package, file an issue and notify the author to update the dependencies. Let's help keep our projects green and our applications secure, performant and bug-free!
npm install duplicate-package-checker-webpack-plugin@^2.1.0 --save-dev
npm install duplicate-package-checker-webpack-plugin

No vulnerabilities found.
Reason
no binaries found in the repo
Reason
license file detected
Details
Reason
Found 4/30 approved changesets -- score normalized to 1
Reason
0 commit(s) and 0 issue activity found in the last 90 days -- score normalized to 0
Reason
no effort to earn an OpenSSF best practices badge detected
Reason
security policy file not detected
Details
Reason
project is not fuzzed
Details
Reason
branch protection not enabled on development/release branches
Details
Reason
SAST tool is not run on all commits -- score normalized to 0
Details
Reason
91 existing vulnerabilities detected
Details
Score
Last Scanned on 2025-07-07
The Open Source Security Foundation is a cross-industry collaboration to improve the security of open source software (OSS). The Scorecard provides security health metrics for open source projects.
Learn More